Deep Instinct x SASETY

First protection solution using Deep Learning
Deep Instinct is the only cybersecurity specialist to apply Deep Learning to protect organizational assets: workstations, servers, smartphones.
Deep Learning is inspired by the learning capacity of the human brain.
When a brain learns to identify an object, its identification becomes natural.
Likewise, as Deep Instinct's deep artificial neural network learns to prevent different types of cyber threats, its prediction capabilities become instinctive.
All types of malware, known or zero-day, ransomware and advanced persistent threats (APT) are anticipated and prevented in real time, with unparalleled accuracy and speed via multi-layered protection covering the entire enterprise, whether whether it's the network, terminals or mobile devices.
Prevent RANSOMWARES attacks
Deep Instinct analyzes, predicts and prevents all malware or malicious files that are still unknown, such as
ransomware, and stops the threat before it executes. This means that the ransomware doesn't even get a chance to penetrate the network.
Organizations don't have to fear encryption or exfiltration
of their files.
PERFORMANCES
> 99%
Accuracy against unknown threats and
0-day
<20ms
Threat detection time
1 to 2
Number of updates needed per year
<0,1%
False positive rate
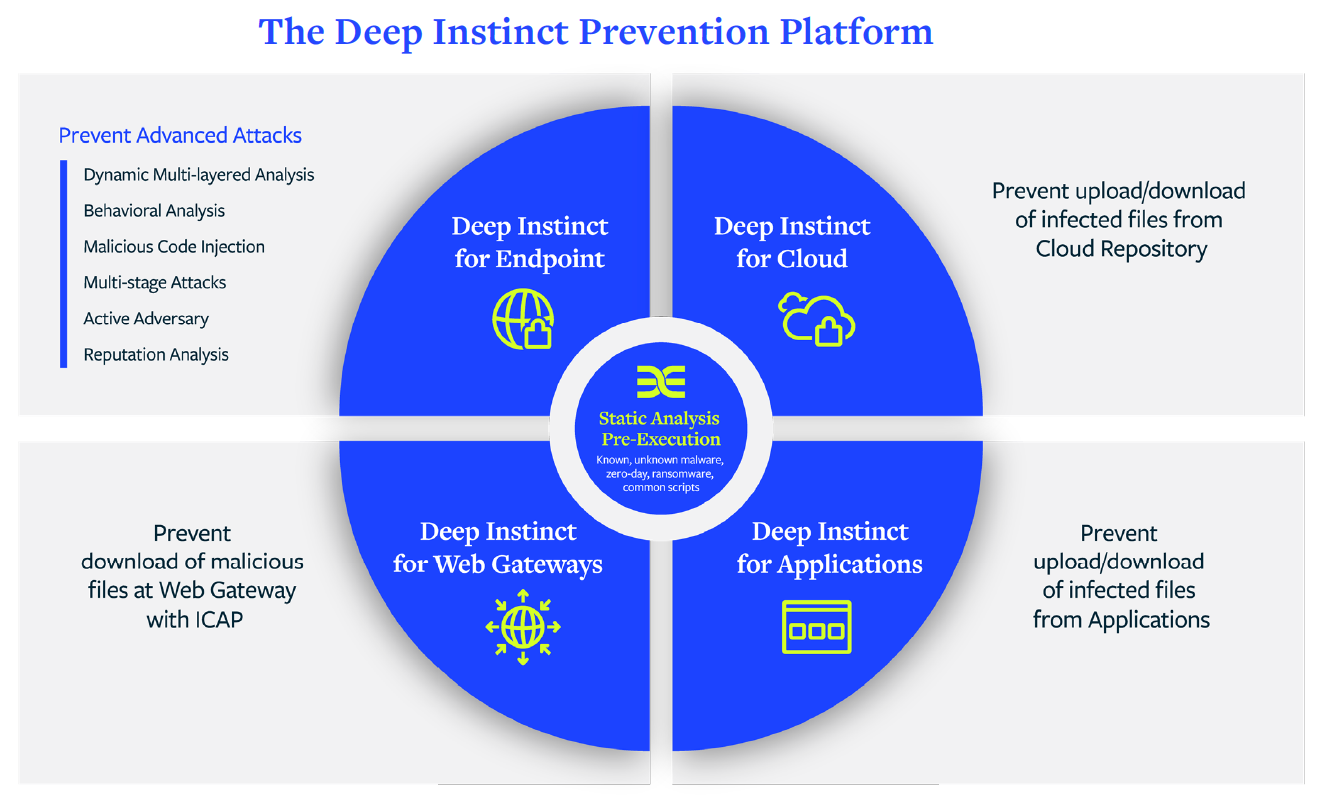
Solution Architecture
Deep Instinct MSP Partner
SASETY supports its customers in the deployment of the solution
Deep Instinct, monitoring and remediation actions
Deployment
- Definition of user groups and associated security policies
- Deployment of the client on different environments: Windows, MacOS, Linux, Android, Chrome & iOS
- Gradual implementation of the detection and prevention strategy:
- Analysis of files and executables
- Behavioral analysis
- Analysis suspicious activities
- Script analysis (macros, PowerShell, HTML Apps & Javascripts)
Supervision
- Identification of suspicious events
- Analysis of the threat: type, severity, source, file, path
- MITRE ATT&CK pointers: tactics and technique used
- Stages of the event and actions carried out on the files (deletion, restoration, quarantine)
- Activity reports
Remediation
- Remote deletion of malicious filesStopping of processes associated with the threatIsolation and reinsertion of affected equipmentExporting files for further investigation and forensic approach








